
Over the past 5 years malware attacks have increased over 10% In the economy leading large and small corporate businesses to worry about their private data security. In this video we’ll be explaining 3 main methods to identify and terminate any malware attacks before they become vital to your computer. If left unattended for some time, malware viruses can corrupt and damage sensitive data that are stored in your PC. Recent cybersecurity reports indicate that the financial impact of these attacks has surpassed $6 trillion annually worldwide, with the average data breach costing companies approximately $4.35 million. What's particularly concerning is that attackers are becoming more sophisticated, using advanced techniques like polymorphic code that constantly changes its signature to evade traditional detection methods. Small businesses are especially vulnerable, with 43% of cyber-attacks specifically targeting them, yet only 14% are adequately prepared to defend themselves.
The three critical detection and removal methods, including signature-based identification, behavioral analysis, and system integrity monitoring. Each approach offers unique advantages in identifying different types of threats, from known malware variants to zero-day exploits that haven't been previously documented. We'll demonstrate how to implement these methods using both built-in operating system tools and third-party security solutions, ensuring you have multiple layers of protection.
Beyond detection and removal, essential preventative measures like establishing proper access controls, implementing regular backup protocols, and creating an incident response plan. The reality is that modern malware doesn't just target your files—it can compromise your entire network, steal customer information, lock you out of critical systems, and even use your infrastructure to launch attacks on others.
About Malware Protection
- Types of malware
- Ransomware that encrypts critical files
- Spyware that steals sensitive information
- Trojans that create backdoor access
- Fileless malware that operates in memory without leaving obvious traces
- Detection methods
- Signature-based detection using known malware patterns
- Behavioral analysis that spots suspicious activity
- Machine learning systems that identify anomalies
- Network traffic monitoring for unusual data transfers
- Prevention strategies
- Regular software updates and patch management
- Employee security awareness training
- Multi-layered security approach (firewall, antivirus, email filtering)
- Regular data backups with offline copies
- Response procedures
- Immediate isolation of infected systems
- Proper incident documentation
- Recovery from clean backups
- Analysis to prevent future incidents
Here are the methods to check if your PC has been affected by Malware and furthermore the steps to remove them.
- Windows Defender Security
The most ethical and traditional antivirus guard that is available in every windows computer is the windows defender security. This is an inbuild security application that is offered free of charge.
Open windows defender

open virus and threat protection
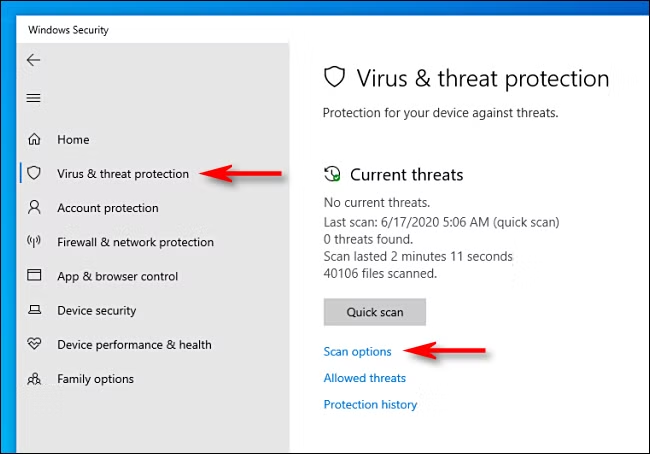
conduct a quick scan and follow the machines further steps to eliminate found issues.
2. Run command
Every windows computer has an inbuild virus scanner. This scanner could be access via a windows run command.
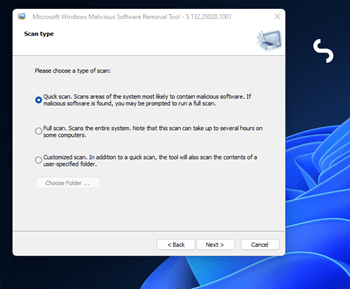
Open windows Run command dialog box (Windows key + R)

Type “mrt” and select ok

You’ll be asked to authenticate access to “Microsoft Windows Malicious Software Removal Tool”. Once access is given, the application will be opened. (you need to be logged in as an administrator)

Select the type of scan and continue
3. 3rd Party Antivirus Software’s
When getting a 3rd party antivirus software, always make sure to purchase an authentic license without getting a crack version. When a third-party antivirus is installed, the ongoing antivirus must be disabled to activate the newly purchased one.
Top 4 best Ranking antivirus software’s to be purchased in year 2025:
- Bit Defender Antivirus Plus
- Norton Antivirus Plus
- McAfee Antivirus
- TotalAV Antivirus



Neither less the most trusted and valid software that is free and trustworthy is windows defender. We hope you gained a certain idea of what needs to be done in order to prevent a malicious software attack’s and we’ll see you in the next article.
